4 Key Risks We Solve

Inability to detect lateral movement across SaaS, identity, and cloud threats
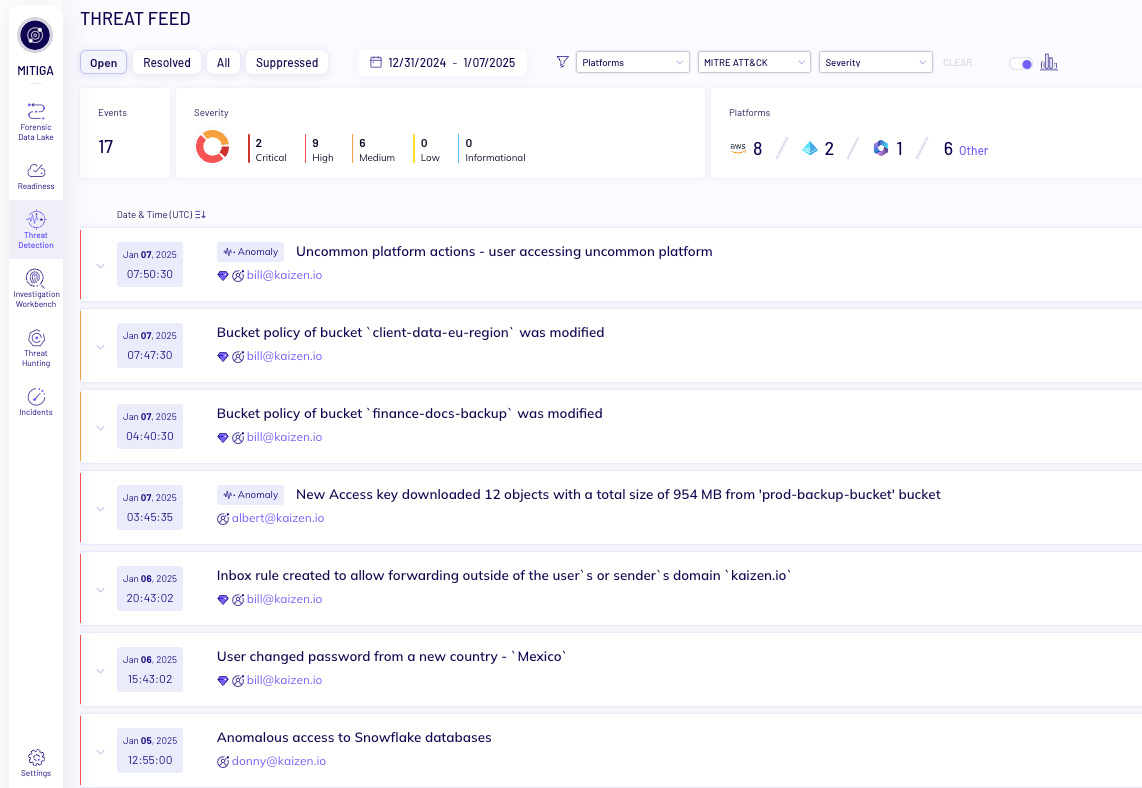
Mitiga provides a unique panoramic view across your cloud and SaaS estate. We combine data from numerous cloud sources into a single dashboard, delivering real-time visibility across your entire cloud footprint.

Manual processes take hours to stitch together attack paths
Mitiga automatically combines and correlates threat signals into a single thread, with our proprietary detection logic engineered specifically for the cloud, saving your team precious time and speed to response.

Lack of cost-effective data readiness
Mitiga enables significant cost savings with our revolutionary approach to cloud data storage. With unlimited forensic data storage, your team gains comprehensive data readiness and contextual insights in case an incident occurs.

Shortage of SaaS and cloud expertise
Mitiga’s team of experts complement your SOC team with Incident Response, Threat Hunting, and optional Managed Services for our platform.


"When something bad happens and you need to activate Mitiga, within an hour they already have people looking at your logs for the past year or even more."
Trusted by leading modern enterprises
Industry Recognition

2024 RSAC Innovation Sandbox Finalist
Mitiga’s innovation earns recognition in the most prestigious cybersecurity competition.

The 10 Hottest Cloud and AI Security Startups
CRN lists top 2024 startups that exemplify the innovation and momentum it takes to become lasting players in the market.

2024 SC Award Finalist: Best Emerging Technology
SC Media applauds cutting-edge technology innovators for their solutions that address ever-evolving threats.
See What Mitiga Can Do
Ready to catapult your SOC into the cloud era? Learn what the Mitiga platform and managed services can do for your SecOps team by meeting with one of our experts.










.svg.png)







