SNOWFLAKE CUSTOMERS
SNOWFLAKE CUSTOMERS
Find out fast if you are impacted by this active threat campaign. >>Cloud Detection and Response (CDR)
Find and eliminate sophisticated cloud threats before they escalate, across your clouds, identities, and SaaS applications.
Reduce false positives | Lower dwell times | Root out persistent threats | Limit breach impact

“Existing CDR tools often overemphasize the detection phase while overlooking the overhead these detections place on SecOps teams, who require efficient categorization and prioritization of threats, as well as tools to accelerate triage and investigation in a relatively new space. Our CDR solution was made to ensure SOC teams can mitigate threats at the scale, speed, and complexity of the Cloud.”
Amir Gabrieli, VP of Product
Mitiga
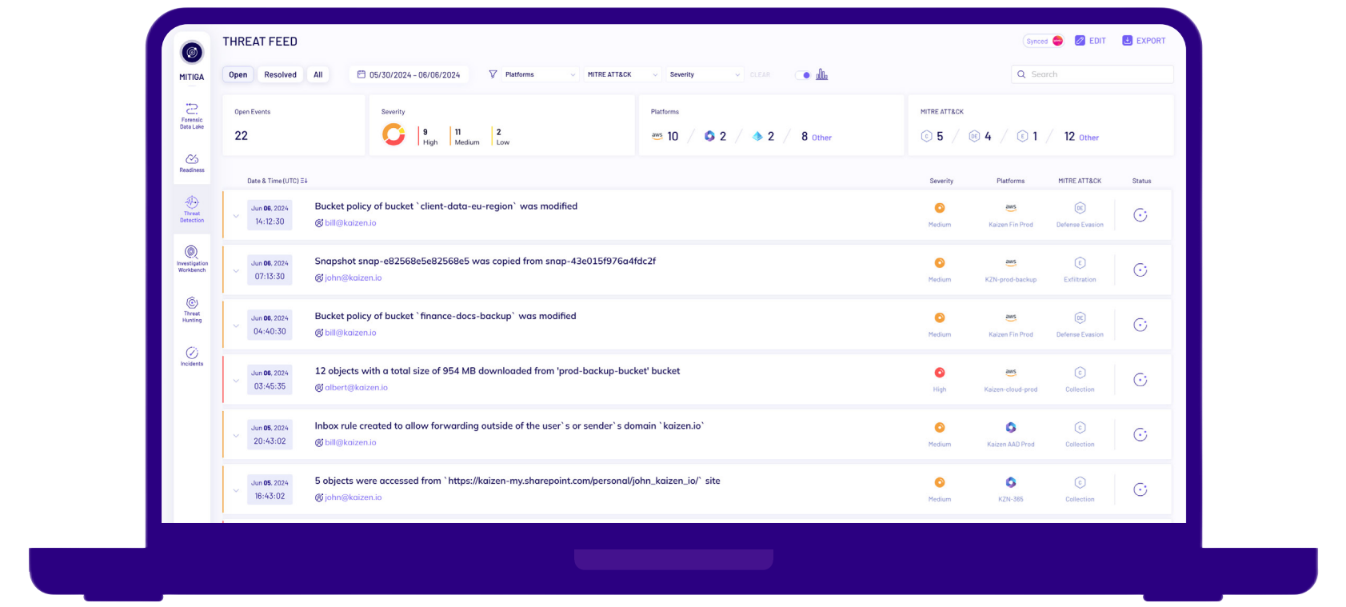
What is Mitiga’s Cloud Threat Detection (CDR)?
Mitiga's CDR delivers unparallelled visibility, faster triage, and deeper investigation capabilities to help teams detect unauthorized activities, data breaches, and insider risks early, uncovering sophisticated threats that traditional tools may miss.
Most existing solutions rely on basic monitoring tools or SIEM platforms with limited cloud-specific capabilities. Mitiga’s platform was designed by cloud experts specifically for cloud and SaaS threats.
Most existing solutions rely on basic monitoring tools or SIEM platforms with limited cloud-specific capabilities. Mitiga’s platform was designed by cloud experts specifically for cloud and SaaS threats.
How we do it.

A Deeper, Wider Data Lake
Our cost-effective Cloud Security and Forensics Data Lake aggregates information about assets and activities across your clouds, SaaS applications, and human and non-human cloud identities to provide a panoramic view and rich context for your investigations.

Advanced Detection Methodologies
We use techniques including anomaly detection and machine learning to analyze cloud assets, cloud activities, and the behavior of human and nonhuman identities to zero in on anomalies and security threats. Our approach offers a level of breadth and granularity most other solutions are missing.

Reflecting the Latest Threat Intelligence
When new threat campaigns start in the wild, our team swiftly develops indicators of attack (IOAs) to run against all customer data, keeping SOC teams at-the-ready to root out emerging threats.

