The Cuba Ransomware Crisis
Ransomware is not a new attack path, or a trend, and most companies have already learned how to protect themselves against it. But every once in a while, ransomware manages to infiltrate and cause damage.This rising trend paved the way for ransomware groups, malicious entities that aim to spread malware across the internet and earn money by blackmailing those unfortunate ones who clicked on the wrong link. One of these groups is called “Cuba Ransomware Gang”, a group that hijacks information and blackmails companies to pay in Bitcoin or watch their disclosed and private information leaked for all to see.
Even though the group was secretive until lately, they now encourage people to visit their site and view the disclosed information or even buy sensitive information that may assist with phishing and spear phishing attacks. Recently, the Cuba gang successfully assaulted a payment processor based in the US, stealing data and causing damage to sites. Their attacks can be devastating, but they can also be efficiently prevented.
Mitiga is well aware of this gang and was summoned to consult several companies that were attacked by Cuba Ransomware Gang. Using these assessments, the Mitiga IR Team was able to piece together the most complete picture of Tools, Tactics, and Procedures (TTPs) used by Cuba and create a prevention plan against them.
The Cuba Ransomware Threat
In one example, Mitiga was called to investigate a ransomware attack on an entertainment company that discovered all its files were encrypted with the ‘.cuba’ extension. The company was sent a ransomware note by the threat actors, demanding a particularly high ransom to decrypt the files.
Here is a redacted version of it:
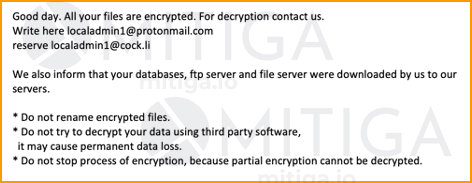
Shortly afterwards, the threat actors sent a second message to the company, indicating they not only encrypted the files, but also exfiltrated a trove of data, including images of passports, credit cards, and the company’s source code itself.
Here is a redacted version of this second email:
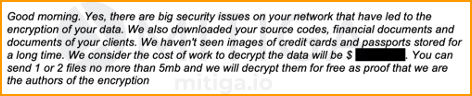
As Mitiga’s forensic analysts began investigating, they found the attackers were active in the network for at least two weeks before the encryption itself. During this time, it was determined, the attackers both established a foothold in the network and exfiltrated the sensitive data.
The Cuba Ransomware Gang's Way
Mitiga’s analysis determined that the Cuba ransomware group leverages publicly available implants and frameworks, embracing the ‘Living-off-the-Land’ approach. More specifically, they used the following TTPs, presented for convenience in the MITRE ATT&CK’s framework:
While the initial infection vector remains unknown, the Mitiga IR team believes the attackers may have used spam and phishing messages to gain access by searching for exposed attack surfaces. These may have potentially included the use of common 1-day RCE vulnerabilities that are still effective against unpatched systems.
In Summary:
- The Cuba ransomware group demanded what is, based on Mitiga's experience of dozens of ransomware cases, a significantly high 8-digit USD amount, which should be paid in BTC.
- Data was successfully exfiltrated, including PII (personally identifiable information) and source code.
- Evidence related to the C2server suggests that the Cuba group is linked to Russia.
- The group employs a Living-off-the-Land (LotL) approach, i.e., using publicly available implants and techniques.
- Mitiga discovered a method to counter an active Cuba attack, preventing files from being encrypted. If you believe you are a target or would like to act preventively, contact us: here.
There are additional details Mitiga’s specialists have discovered that can be made available on a limited and verified basis. If you are a security professional and would like access these additional insights on our findings regarding the Cuba ransomware group, you may request them here.

LAST UPDATED:
November 7, 2024


