What Happened With the Log4j Library?
Security teams all over the world are rushing to deal with the new critical zero-day vulnerability called Log4Shell. This vulnerability in Apache Log4j, a popular open-source Java logging library, has the potential to enable threat actors to compromise systems at scale.
What Do You Need to Know?
- The Log4Shell security vulnerability is rather easy to exploit
- Threat actors are actively compromising vulnerable systems as we speak
- There is a security patch available and also a myriad of quick fixes and remediations
- Organizations should identify assets that use the Log4j library and patch them immediately
What Is the Scope of the Log4j Vulnerability?
Log4j is one of the most popular Java logging libraries, used by a vast number of applications. Threat actors attempted to use this exploit on more than 31.5% of corporate networks globally, according to Check Point Software.
Large companies and enterprises, such as Amazon, Apple, Twitter, CloudFlare, Steam, and Baidu have servers vulnerable to this attack, according to a GitHub repository. Additionally, more than 200 global companies and manufacturers have already published security advisories and bulletins according to this list.
Leveraging this critical vulnerability, attackers can anonymously exploit remote systems. The scope, impact, and scale are incomparable to anything the security industry has seen in the past few years.
What Are the Technical Details?
CVE-2021-44228 (aka Log4Shell) is a Remote Code Execution (RCE) vulnerability in Apache Log4j, a ubiquitous library used for logging by many Java-based applications. Versions 2.0-beta9 to 2.14.1 are affected by this vulnerability.
By exploiting it, an attacker can execute malicious code on a server that runs a vulnerable version of Log4j. The steps are simple:
- Malicious Request: The attacker targets the victim server and sends a specifically crafted malicious request (usually, HTTP)
- Request: Within the victim's server, the vulnerable Log4j utility is triggered by the malicious request to query the attacker's malicious server.
- Response: Attacker's server sends its malicious payload in its response; vulnerable victim server executes payload.

What Is the Log4j Incident Timeline?
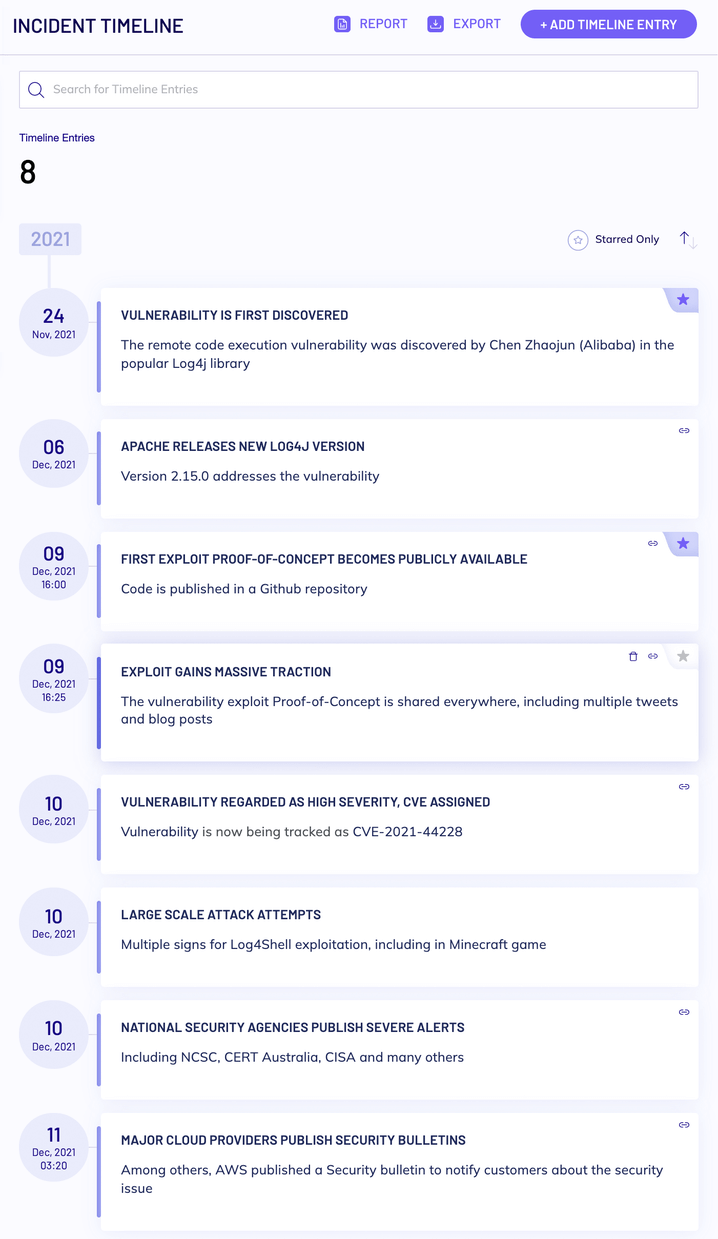
The Bad News
Offensive teams were quick to develop exploits to this security vulnerability and use them at scale.
However, DevOps and security teams are struggling to discover, orchestrate, patch, remediate, manage, prioritize, monitor, detect, and respond.
Unfortunately, the abundance of content, security advisories, detection rules and blog posts only makes it harder to keep up with the pace, prioritize effectively, and make informed decisions.
The Good News
We at Mitiga curated a list of security resources to help you with your efforts: Detections, remediations, IoCs, notable blog posts, and more.
We will constantly update this blog post and the attached list and help you focus on the important things.
And Finally: The List of Everything, Including Log4j Vulnerability Fix
Following is a link to our Github page:
https://github.com/mitiga/log4shell-everything
Contributors: Eitan Freda, Adi Belinkov, Nir Ben Eliezer

LAST UPDATED:
November 12, 2024


