It’s official: Gem Security is joining CNAPP decacorn Wiz. Acquisitions in tech do not happen by accident, but rather because giants in the industry recognize the gaps they need to fill as rapidly as possible.
In this blog, I will explain what this acquisition means for the future of cloud security so you understand where the industry is headed and what questions you should be thinking about as you selectively choose cloud security vendors.
Wiz Officially Acquires Gem Security to Boost Its CNAPP Offering
Wiz CEO Assaf Rappaport mentioned the following in his LinkedIn post: “It feels like the missing piece of the puzzle has finally fallen into place.”
On a fundamental level, CNAPPs are incomplete without strong cloud threat detection, investigation, and response capabilities. The claim of offering end-to-end security in the cloud cannot be truly complete without both prevention and detection and response in mind, a glaring “missing piece” CNAPPs have not been able to tackle well.
As a co-founder of Mitiga, it makes me proud that CNAPP teams recognize this missing puzzle piece as a “right now” problem rather than a “for later” problem. This is pure validation that as the number of cloud breaches continues to increase with each passing year, prevention is no longer enough. Saying “cloud” when it does not include cloud as a whole – across IaaS, PaaS, and SaaS – is not enough either.
Strategically, there are several points you should consider when it comes to Gem as an option for your organization’s cloud threat detection, investigation, and response. Even with the market validation that this acquisition brings to our space, it is still important to be aware of the ways in which Gem won’t solve Wiz’s CDR/CIRA gap.
Reasoning Behind the Gem Acquisition
In Wiz’s blog announcing the acquisition, the headline reads: “We’re pushing for consolidation, bolstering our Cloud Detection and Response capabilities, and delivering on the promise of security operations for the cloud era.”
The blog goes into further detail for each of these areas, but the overall points are important to analyze and compare against the reality of the cloud security industry:
1. Pushing for consolidation: Complete consolidation is far from possible at this point in cloud security no matter how long we have been striving for it. The “consolidation” we have so far includes acquisitions or building basic in-house capabilities. However, we all know that smooth integration with the wider ecosystem is more realistic than consolidation. Until cloud security platforms can create a full suite of sophisticated solutions in-house, “consolidation” should still be used loosely, and it will remain to be seen if this acquisition will improve or delay progress within the security ecosystem.
2. Bolstering CDR capabilities: More on this later, but CDR lacks a critical component in the management of cloud breaches: investigation. Gem is not equipped to help Wiz solve this issue, which leaves a gap in where the market is headed and a reason why Gartner created a new category called CIRA to address this directly.
3. Delivering on the promise of security operations for the cloud era: I argue that any cloud security company would agree with this statement – I certainly do. SecOps was not inherently designed for sprawling cloud footprints, and SOC teams and CISOs need support taming the growing number of threats their organizations face.
Why Gem Security Will Not be Enough for Wiz to Close the Gaps
As I mentioned earlier, I am thrilled to see the industry understand that CNAPPs alone are ill-equipped to prepare their customers for modern cloud security threats. However, Gem Security joining Wiz is not going to be the answer that customers are ultimately looking for because of the critical needs left unmet based on Gem’s capabilities.
Addressing the Entire Cloud Threat Detection, Investigation, and Incident Response Spectrum
Mitiga’s roots are in incident response for cloud and SaaS. While our technology is there to enable everything a SOC needs to be fully capable in the cloud, our team conducts hunts every day inside client environments and is ready to respond to any incident that arises.
Our expertise naturally drew us to threat detection and building the investigation capabilities needed to investigate cloud attacks. Now, Mitiga offers end-to-end cloud threat detection, investigation, and incident response for customers, addressing the full lifecycle of the “response” side of cloud security (as opposed to the prevention side that CNAPPs cover).
Gem, meanwhile, was born as a Cloud Detection and Response company. It is a self-service tool for SecOps rather than a full detection and investigation platform. Ultimately, this leaves them incapable of continuing to build the knowledge and expertise that is required to keep up with cloud threats. When a major cloud breach happens, incident response is critical, and Gem customers (now becoming Wiz customers) will still need another vendor to address that need. As we can see again, then, the term “consolidation” must be used loosely.
Breadth of Coverage
Gem covers major cloud providers and some identity providers, but not office suites or SaaS. With over 70 cloud, identity, and SaaS adapters including all major cloud service providers, Salesforce, Office 365, and more, Mitiga achieves both breadth and depth in the arena of visibility into cloud threats.
This is why it is so critical that potential and existing customers of Wiz and Gem obtain specific answers regarding what “cloud” really covers. While every company in our space has different capabilities in terms of coverage, customers will all agree that breadth and depth of coverage should always include more, not less or the bare minimum.
Lack of Strong Threat Investigation Competency
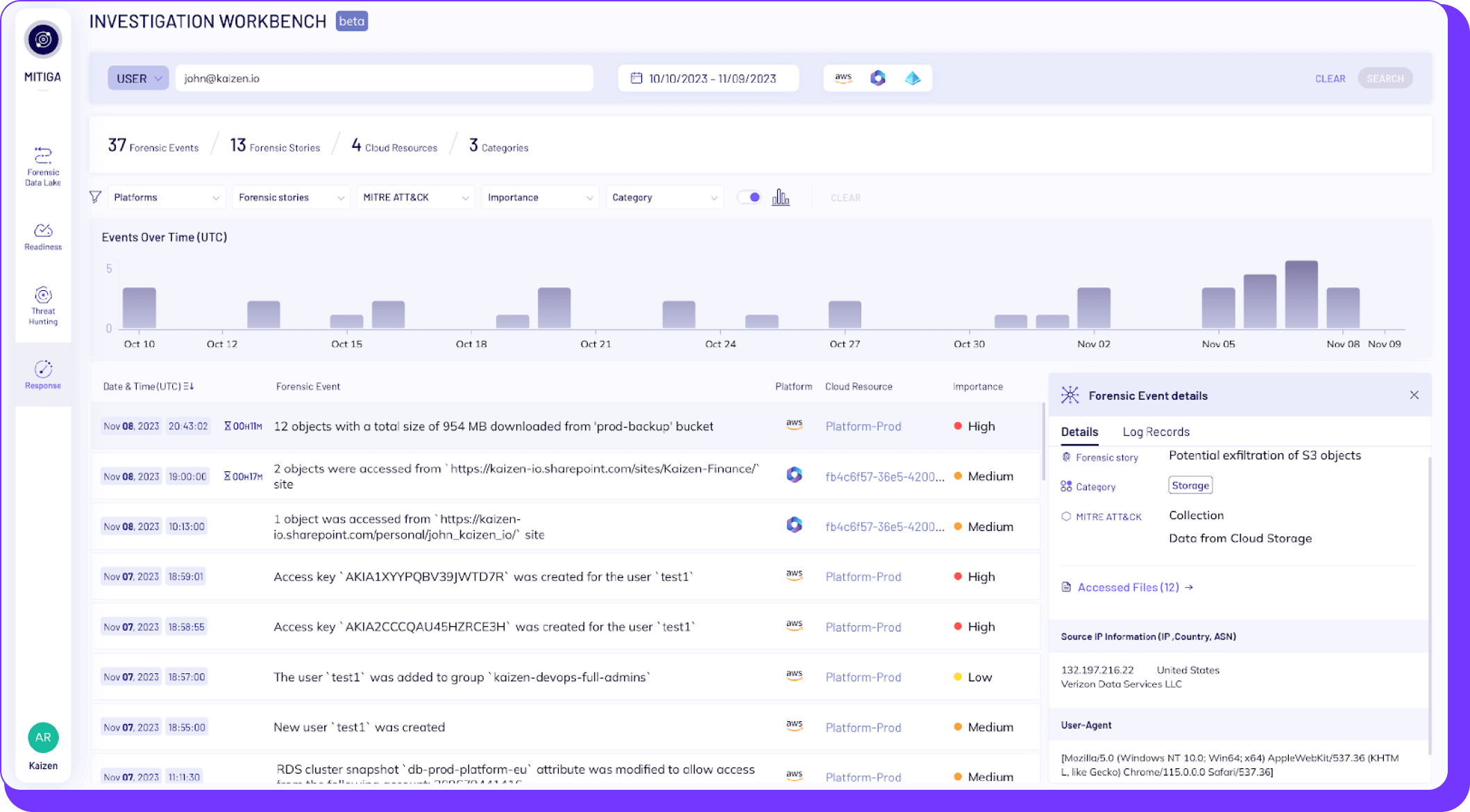
Learning what happened and piecing it together into a straightforward narrative is a must-have. With Gem, customers can see the raw logs and information of what occurred. With the Investigation Workbench in Mitiga, we provide that as well as the extra layer of context that answers the question of “What is the story here?” This allows our customers to see a full picture of what occurred rather than having only the relevant data but still needing to piece it together themselves.
A New Era of CNAPPs and Cloud Security Is Here
Mitiga is doing to SecOps what CNAPPs did for posture and vulnerability management. It is clear that SecOps has largely been ignored with the rise of cloud, but the time to address that gap is not later – it is now.
CNAPPs are aiming to start addressing what customers have been asking for, which is to help them detect, investigate, and respond to threats in a manner purpose-built for the cloud. Additionally, the era of believing that prevention is enough is over, and modern SOC teams deserve the best support to help their companies operate confidently in the cloud.
Questions about the Gem acquisition? Get in contact with one of our cloud security experts today or set up a demo to see how your team can take your cloud threat detection, investigation, and response to the next level.
LAST UPDATED:
September 24, 2024


